Recurring pain points
- Unable to track threats from outside of the network
- Lack of up-to-date threat information
- Difficulties in identifying threats behind indicators
- Coding automations tasks is time consuming
- False positives and false negatives hinder efficient threat detection
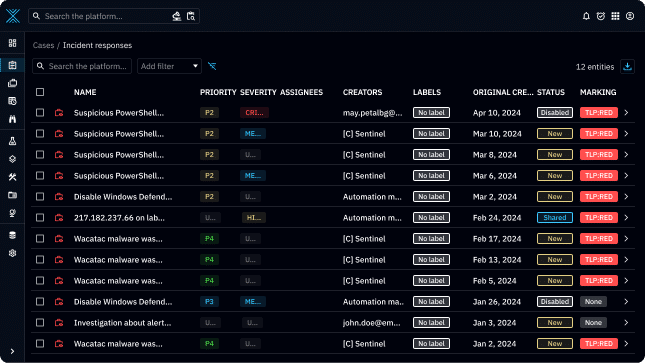
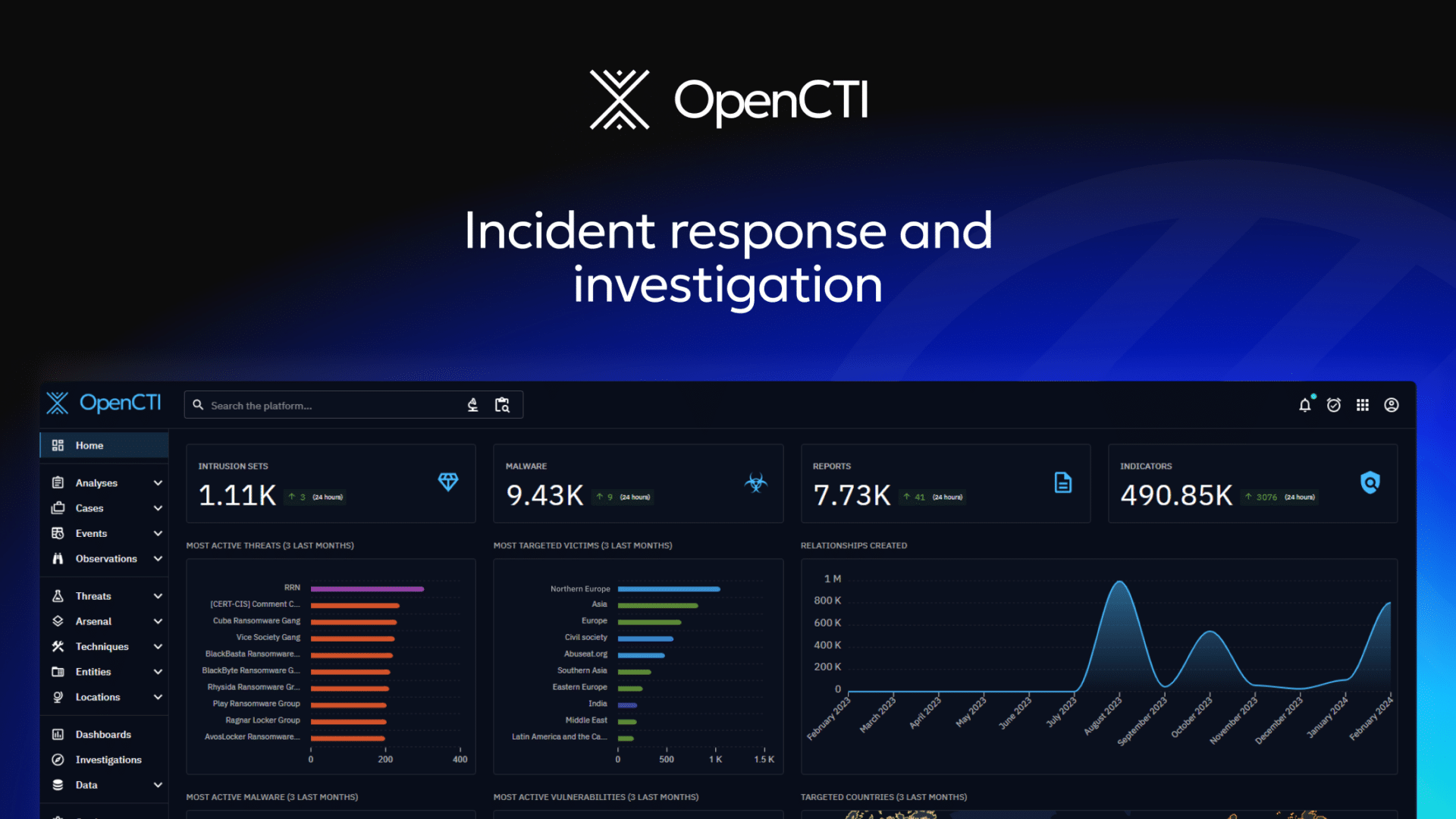
Comprehensive alert collection
Focus on relevant alerts rather than the entirety of your activity logs. By pushing cyber threat alerts from your SIEM or XDR to OpenCTI, your SOC team enhances its ability to analyze internal and external threats comprehensively.
Adopting an intelligence-driven approach enables SOC teams to implement proactive threat detection and prevention strategies. OpenCTI ensures that your security tools are automatically updated and optimized in real time.
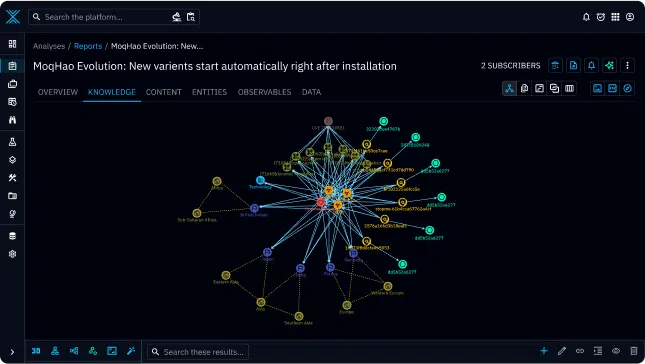
Advanced threat identification
Leverage STIX 2.1 framework and graph-based visualizations to classify threat intelligence and visualize entities and their relationships in a dynamic knowledge graph. This help SOC teams to easily pivot from entity to entity, for example from an IP address to a malware to a threat actor.
Configure inference rules to automatically create logical STIX relationships, save the analyst’s time and reinforce the graph’s quality.
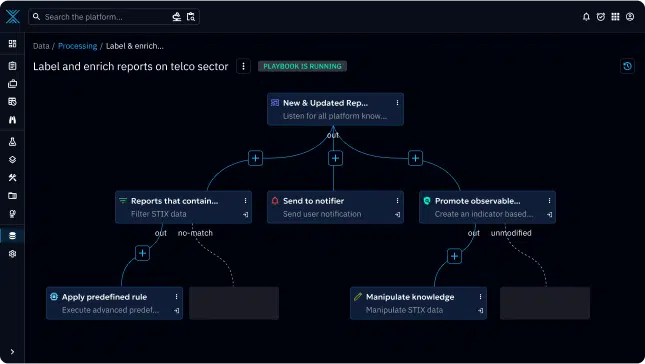
No-code automation playbook
Program step-by-step playbooks with a few clicks to automate a series of manual tasks including but not limited to threat intelligence enrichment, data manipulation, data filtering and notification delivery.
Our no-code automation playbook allows cybersecurity teams to quickly schedule repetitive but necessary tasks without the need for in-depth coding skills.
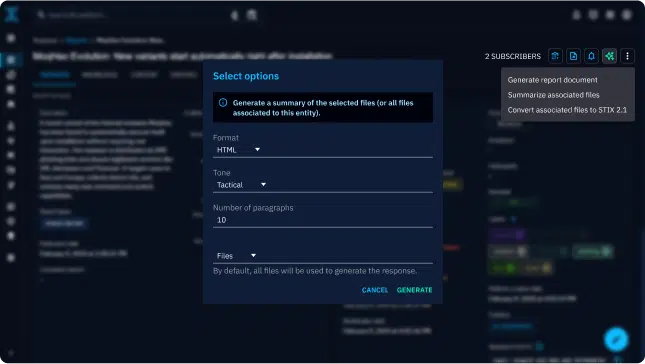
Faster threat detection with Generative AI
Utilize our generative AI tool, “Ask AI”, in OpenCTI to effortlessly convert structured information to unstructured data and vice versa.
Trivialize time-consuming tasks such as reading reports and deciphering threat data into actionable intelligence. This enables SOC teams to focus their efforts on implementing customized threat detection strategies and analyzing their results.