Recurring pain points
- Hard to create and share report with security teams and across platforms
- Difficulties in qualifying alerts raised by detection systems
- Poor organization between incident responders during incident management
- Significant workload to gather and format the findings of the investigation/incident response
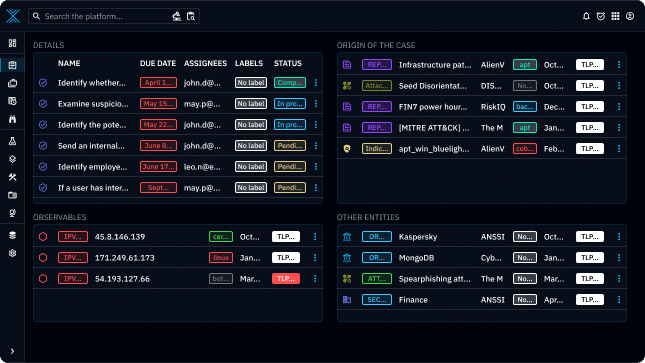
Incident creation and tracking
Initiate a new case to document and oversee a specific security incident or threat, all while assigning team members. This case serves as a centralized repository for all relevant incident-related information.
Keep it up-to-date with new findings, developments, and actions taken, enabling clear tracking of the incident’s status and response efforts.
Collaborative workspace
Team members can collaborate in real-time, while sharing insights, observations, and analysis related to the incident fostering teamwork and knowledge sharing.
Tasks can be assigned to specific users directly from the case, ensuring every aspect of the incident is addressed.
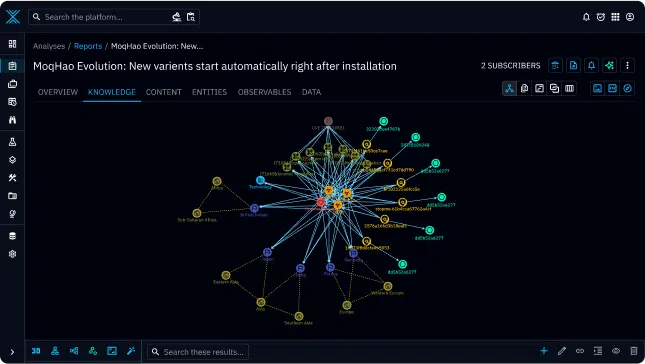
Graph and knowledge
Bring together diverse sources of information into a single, centralized location. All the knowledge contained can be visualized in comprehensive graphs so users can see relationships between entities, get a global view of the incident, and better understand context and actions that should be taken.
Timelines and correlations with other cases are also available to represent the chronological sequence of events related to the incident.
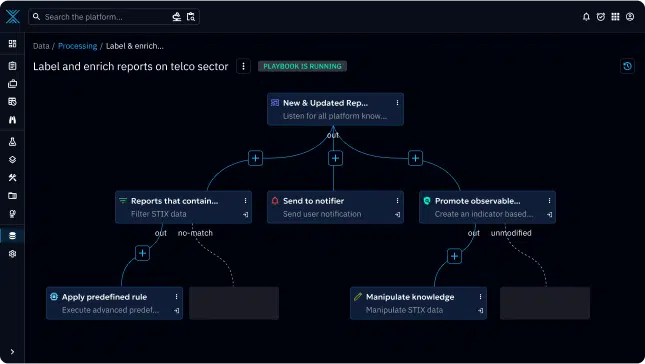
Automated workflow
Replace manual tasks with intelligent, real-time automation. Automated workflow streamlines operations, prioritizes critical threats, and reduces response times. Traditional methods often resulted in lengthy processes, leaving systems vulnerable for extended periods.
Using automation for malware detection, incident triage, playbook execution, and documentation, significantly improves response times, alert prioritization and reduces the burden on security teams.